TL;DR: a transparency-enhancing feature of iOS has revealed data handling practices of a load of app providers and those practices did not sit well with users, even leading to the filing of a class-action lawsuit. In the light of those revelations, I use this blog post to provide a little background on the less-known privacy tools Transparency-Enhancing Technologies (TETs).
Clipboard Stealing Apps
Recently, Apple introduced a transparency feature to the upcoming iOS 14 that notifies users whenever an app accesses the clipboard’s content. You can watch a video of the feature catching a wide range of apps “stealing” clipboard content here. The video shows only a small selection of apps, but other apps have also been found to access clipboard data for dubious reasons, e.g., the linkedIn app in which case even a lawsuit has been filed in the wake of the revelation.
In the light of these events, I want to provide some background on Transparency-Enhancing Technologies, a lesser-known class of privacy tools. Transparency-Enhancing Technologies (TETs) can support in fulfilling the GDPR’s Chapter 3’s obligations regarding information and data subject rights. But aside from compliance, they can also help build user trust and willingness to disclose data. And, finally, as was the case with iOS, some TETs can bring to light other parties’ data handling practices…
What are TETs?
Most people with an interest in information privacy are familiar with PETs, Privacy-Enhancing Technologies. Their siblings TETs, Transparency-Enhancing Technologies, however, are far well less known although they have been enjoying increasing popularity during the last years. For example, some big data-centric players such as Google or Microsoft have (more or less voluntarily) started to adopt TETs. Broadly speaking and inter alia, the GDPR requires data controllers to implement appropriate technical and organizational measures designed to implement the data protection principles. Transparency-Enhancing Technologies aim at one of those principles, namely at the principle of lawfulness, fairness and transparency of data processing (Art.5 GDPR).
Transparency-Enhancing Technologies can be defined as “tools which can provide to the individual concerned clear visibility of aspects relevant to [its personal] data and the individual’s privacy” [1]. Hence, unlike PETs, TETs do not aim at data-minimization but at transparency by providing individuals with insight into a data controller’s intended and actual data handling behavior. Some TETs additionally provide users with functionality for exercising some level of control over the collected data and its usage. For example, a TET can provide users with the functionality to rectify collected data or issue a data subject access request. The depth and width of the insight and control provided by a TET depends on the specific type of TET and the provider’s goals. I won’t go into too much detail on the different types of TETs here but will focus on some examples. If you are interested in a more in-depth discussion of different classes of TETs, you can find here a preliminary classification of TETs I came up with several years ago.
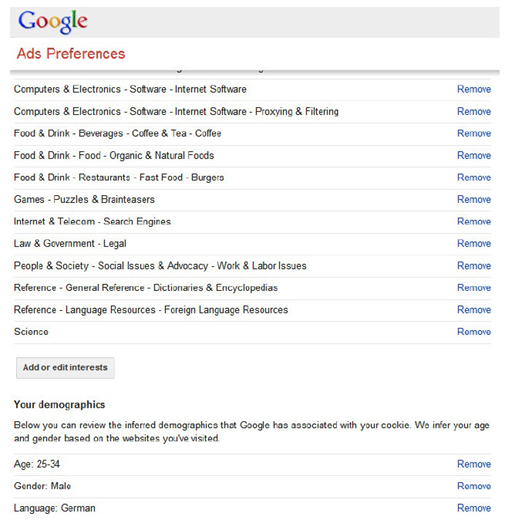
So-called privacy dashboards are probably the most prominent type of TETs. A privacy dashboard constitutes a central access point to privacy-relevant information relating to the user. With a privacy dashboard, data subjects can usually gain insight into the data relating to them held by a data controller and its usage but can also often exercise some control over that data. For example, Google’s dashboard allows users to deactivate the collection of some location data or the storing of search queries. The figure below depicts a small excerpt from a rather old version of Google’s privacy dashboard. The excerpt depicts a subset of the advertising categories and demographic information that Google inferred about the user. As depicted, the user can also remove certain items or add “advertising interests”. Surely, however, the user does not have any guarantees regarding the actual effects of removing or adding data in this specific dashboard.
Why provide TETs?
Transparency-Enhancing Technologies have been provided by a range of parties, ranging from privacy activists (e.g., EFF’s Privacy Badger that also includes blocking and goes beyond merely providing information) to big data-centric players such as Google (see above). While it is obvious why activists and privacy advocates would provide tools to reveal other parties’ data handling practices, why would a data controller go through the hassle of implementing and operating TETs covering its own processing of personal data?
On the one hand, TETs such as Privacy Dashboards can be used to provide users with information on planned and actually performed data processing. Thereby, these tools can support data controllers in fulfilling the transparency obligations laid down in the GDPR. For example (and to some extent), a Privacy Dashboard can be used to provide data subjects with the information they have the right to access pursuant Art. 15 GDPR. It can also be used as a user interface for requests regarding data export and, hence, support data controllers in fulfilling the obligations pursuant Art. 20 GDPR.
On the other hand, transparency and the perception of control over the processing of personal data have been shown to positively influence user trust and willingness to disclose data (see, e.g., [2, 3, 4,] among many others). Additionally, user segments with a high valuation of privacy might, in some use cases, value TETs and the opportunity to exercise control over the processing of their personal data.
Consequently, TETs can be used to support controllers in complying with data protection legislation while at the same time fostering user trust. However, further research is still needed to learn more about users’ preferences and the effects of individual TETs in different use cases and scenarios, e.g., smart homes, connected mobility etc.